Google links new LostKeys data theft malware to Russian cyberspies

Since the start of the year, the Russian state-backed ColdRiver hacking group has been using new LostKeys malware to steal files in espionage attacks targeting Western governments, journalists, think tanks, and non-governmental organizations.
In December, the United Kingdom and Five Eyes allies linked ColdRiver to Russia’s Federal Security Service (FSB), the country’s counterintelligence and internal security service.
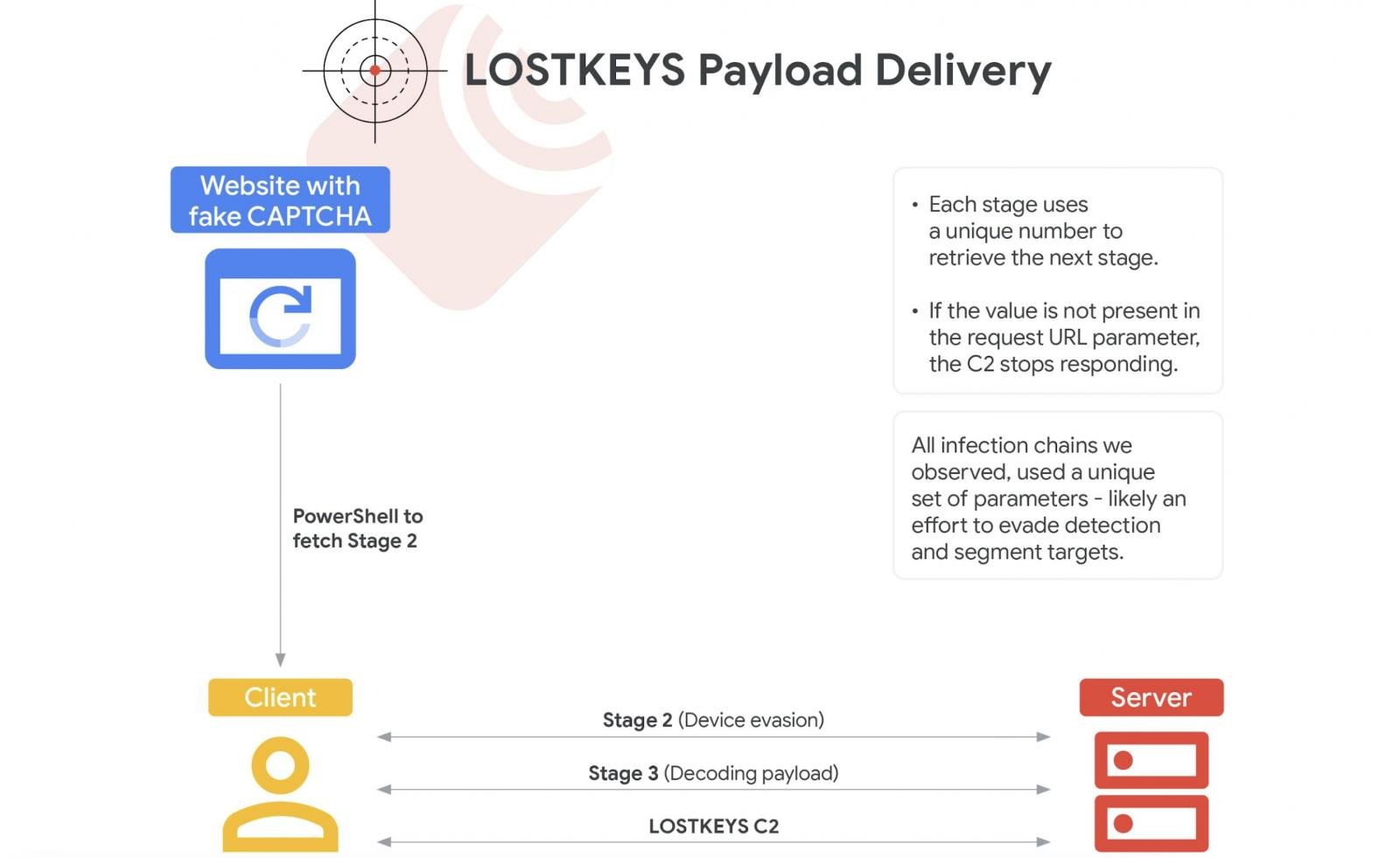
Google Threat Intelligence Group (GTIG) first observed LostKeys being “deployed in highly selective cases” in January as part of ClickFix social engineering attacks, where the threat actors trick targets into running malicious PowerShell scripts.
Running these scripts downloads and executes additional PowerShell payloads on the victims’ devices, ending with a Visual Basic Script (VBS) data theft malware tracked by Google as LostKeys.
“LOSTKEYS is capable of stealing files from a hard-coded list of extensions and directories, along with sending system information and running processes to the attacker,” GTIG said.
“The typical behavior of COLDRIVER is to steal credentials and then use them to steal emails and contacts from the target, but as we have previously documented they will also deploy malware called SPICA to select targets if they want to access documents on the target system. LOSTKEYS is designed to achieve a similar goal and is only deployed in highly selective cases.’
ColdRiver is not the only state-backed threat group hacking into their targets’ devices in ClickFix attacks, with Kimsuky (North Korea), MuddyWater (Iran), APT28, and UNK_RemoteRogue (Russia) having all used these same tactics in espionage campaigns in recent months.
Also tracked as Star Blizzard, Callisto Group, and Seaborgium, the ColdRiver hacking group has used social engineering and open-source intelligence (OSINT) skills to research and lure targets since at least 2017.
Five Eyes cyber agencies also warned in December 2023 of ColdRiver’s spear-phishing attacks against defense, governmental organizations, NGOs, and politicians, months after Russia invaded Ukraine, and these attacks also expanded to targeting defense-industrial targets and U.S. Department of Energy facilities.
In 2022, the Microsoft Threat Intelligence Center (MSTIC) disrupted another ColdRiver social engineering operation where the attackers used Microsoft accounts to harvest emails and monitor the activity of organizations and high-profile individuals in NATO countries.
The U.S. State Department sanctioned two ColdRiver operators (one of them an FSB officer) in December 2023, who were also indicted by the U.S. Justice Department for their involvement in a global hacking campaign coordinated by the Russian government.
The State Department now offers up to $10 million in rewards for tips that could help law enforcement locate or identify other ColdRiver members.
Source link



